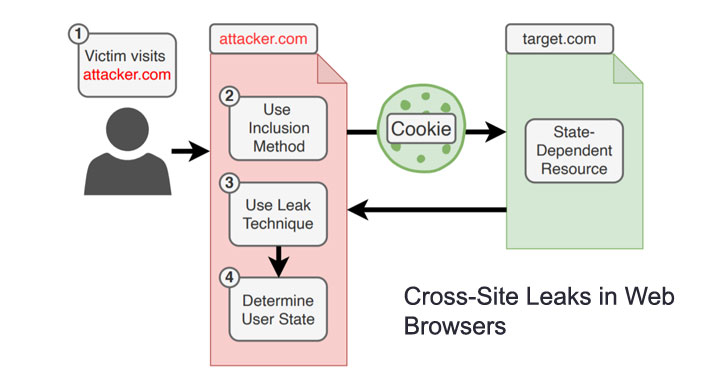
Researchers have discovered 14 new types of cross-site data leakage attacks against a number of modern web browsers, including Tor Browser, Mozilla Firefox, Google Chrome, Microsoft Edge, Apple Safari, and Opera, among others.
Collectively known as "XS-Leaks," the browser bugs enable a malicious website to harvest personal data from its visitors as they interact with other websites in the background without the targets' knowledge. The findings are the result of a comprehensive study of cross-site attacks undertaken by a group of academics from Ruhr-Universität Bochum (RUB) and Niederrhein University.
"XS-Leaks bypass the so-called same-origin policy, one of a browser's main defences against various types of attacks," the researchers said in a statement. "The purpose of the same-origin policy is to prevent information from being stolen from a trusted website. In the case of XS-Leaks, attackers can nevertheless recognize individual, small details of a website. If these details are tied to personal data, those data can be leaked."
Stemming from side-channels built into the web platform that permits an attacker to gather this data from a cross-origin HTTP resource, the cross-site bugs impact an array of popular browsers such as Tor, Chrome, Edge, Opera, Safari Firefox, Samsung Internet, spanning across different operating systems Windows, macOS, Android, and iOS.
The new class of vulnerabilities is also different from a cross-site request forgery (CSRF) attack in that unlike the latter, which exploits a web application's trust in a browser client to execute unintended actions on behalf of the user, they can be weaponized to infer information about a user.
"They are a significant threat to Internet privacy since simply visiting a web page may reveal if the victim is a drug addict or leak a sexual orientation," the researchers explained. "XS-Leaks take advantage of small pieces of information which are exposed during interactions between websites […] to reveal sensitive information about users, such as their data in other web applications, details about their local environment, or internal networks they are connected to."
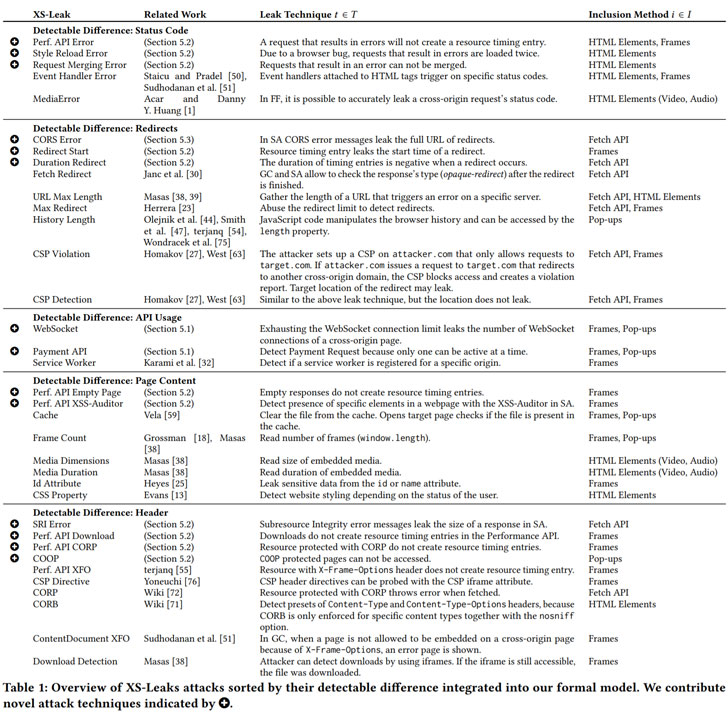
The core idea is that while websites are not allowed to directly access data (i.e., read server responses) on other websites because of same-origin constraints, a rogue online portal can attempt to load a specific resource or an API endpoint from a website, say, an online banking website, on the user's browser and draw inferences about the victim's transaction history. Alternatively, the source of the leak could be timing-based side-channels or speculative execution attacks like Meltdown and Spectre.
As mitigations, the researchers recommend denying all event handler messages, minimizing error message occurrences, applying global limit restrictions, and creating a new history property when redirection occurs. At the end-user side, turning on first-party isolation as well as Enhanced Tracking Prevention in Firefox have been found to decrease the applicability of XS-Leaks. Intelligent Tracking Prevention in Safari, which blocks third-party cookies by default, also prevents all leaks that are not based on a pop-up.
"The root cause of most XS-Leaks is inherent to the design of the web," the researchers said. "Oftentimes applications are vulnerable to some cross-site information leaks without having done anything wrong. It is challenging to fix the root cause of XS-Leaks at the browser level because in many cases doing so would break existing websites."
- Karlston
-

 1
1


Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.