‘TeamTNT’ Has a New Credential Harvester Targeting Cloud Services on the Loose
- ‘TeamTNT’ is using a new harvester that targets a wide spectrum of cloud services and software apps.
- The actors are still targeting Monero wallets and configuration files and are still DDoSing some victims.
- The hacking group that started as an opportunistic actor is now evolving into a serious threat.
‘TeamTNT,’ the hacking group that was mostly occupied with disseminating XMR cryptominers on exposed Dockers last year, is now targeting cloud service credentials. This change in activity was first noticed and reported by researchers at TrendMicro at the beginning of March, and now, the same team has sampled and analyzed a new credential harvester used by the threat actors.
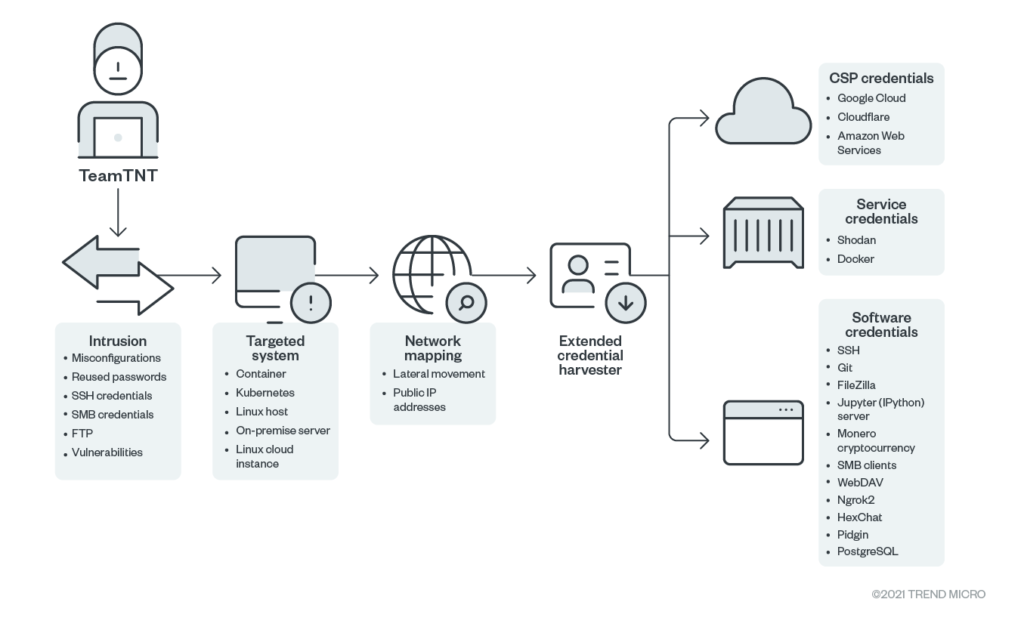
The intruders deploy a rich repertoire to access the network, including the exploitation of vulnerabilities, using stolen passwords or taking advantage of the existence of misconfigurations. From there, they focus on a range of system types depending on what they can find, then perform network reconnaissance, and finally deploy their new credential harvester.
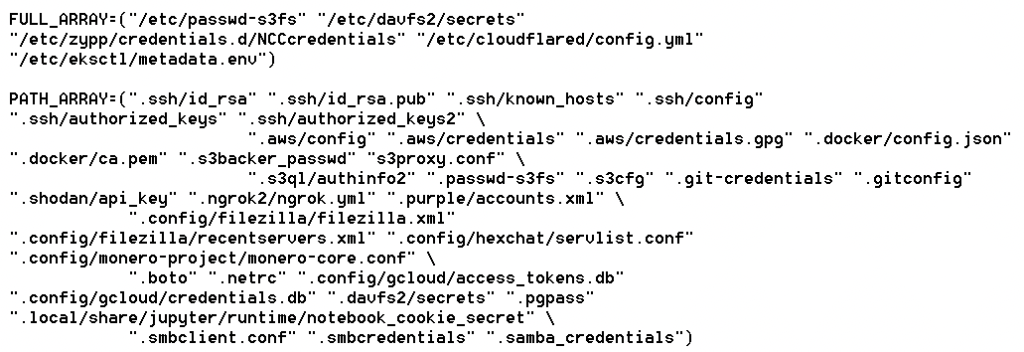
This malware helps TeamTNT steal user IDs and passwords from the following software and services:
- Google Cloud
- Cloudflare
- Amazon Web Services
- Shodan
- Docker
- SSH
- Git
- FileZilla
- Jupyter
- Monero wallet
- SMB clients
- WebDAV
- Ngrok2
- HexChat
- Pidgin
- PostgreSQL
Source: TrendMicro
So, why is TeamTNT interested in stealing cloud service and software app credentials? One very probable reason would be to engage in planting XMR cryptominers in places where they are unlikely to be found and uprooted before making significant amounts of money for the actors. Another would be to resell these credentials to ransomware groups on the dark web. And a third would be to exfiltrate data from cloud-hosted databases and then sell them to phishing actors and scammers.
Source: TrendMicro
TrendMicro points out that the malware actively looks for Monero configuration files and any accessible wallets, so the anonymous crypto remains a key motivation for the actors, or at least that’s what it looks like. When the malware reaches the end of its routine, it attempts to delete itself from the infected system. Still, according to the analysts, this function isn’t implemented properly yet, so it fails.
One more thing to note is that TeamTNT also engages in DDoS attacks once inside a network, as long as they have some form of an RCE to execute it. This is happening through a special IRC bot called ‘TNTbotinger.’ DDoS attacks can help the actors draw the attention of response teams elsewhere, slow down malware detection and clean-up efforts, or even aid extortion efforts.
In general, TeamTNT has evolved into a significant and wide-scope threat now. Their new harvester is an indication that the particular malware authors are serious about their operation and care to take things to the next level.
Source: ‘TeamTNT’ Has a New Credential Harvester Targeting Cloud Services on the Loose



Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.