In December 2024, Microsoft Threat Intelligence identified a malware campaign stemming from pirate streaming sites. Using iframe malvertising redirector URLs to generate revenue, and redirects up to five layers deep, malware payloads hosted on GitHub, Discord and Dropbox, acted as a dropper for additional payloads hosted elsewhere. Microsoft says the goal was to steal information and it believes almost a million devices were infected.
Public pirate sites accessible by anyone with an internet browser have been under financial pressure for years.
Rightsholder-led campaigns urged mainstream advertisers to boycott the platforms to cut off their revenue streams. This was supposed to put sites out of business but in many cases that simply meant the deployment of lower quality ads from any entity still prepared to place them. Sites that used to be relatively safe quickly became relatively unsafe and, as the pressure increased, some became very unsafe indeed.
As reported last week, elaborate and lucrative schemes are able to counter limitations on advertiser choice. Unfortunately, these methods also provide an environment where scams and flat-out malicious activities thrive, before doing the kind of damage reported by Microsoft late last week.
Large-Scale Malvertising Campaign Began on Pirate Streaming Sites
Microsoft’s official report published last week is highly detailed and by its own accounting, a full 32-minute read. We’ll distill the key details here.
Early December 2024, Microsoft Threat Intelligence identified a large-scale malvertising campaign that it now believes infected almost one million devices for the purpose of stealing information.
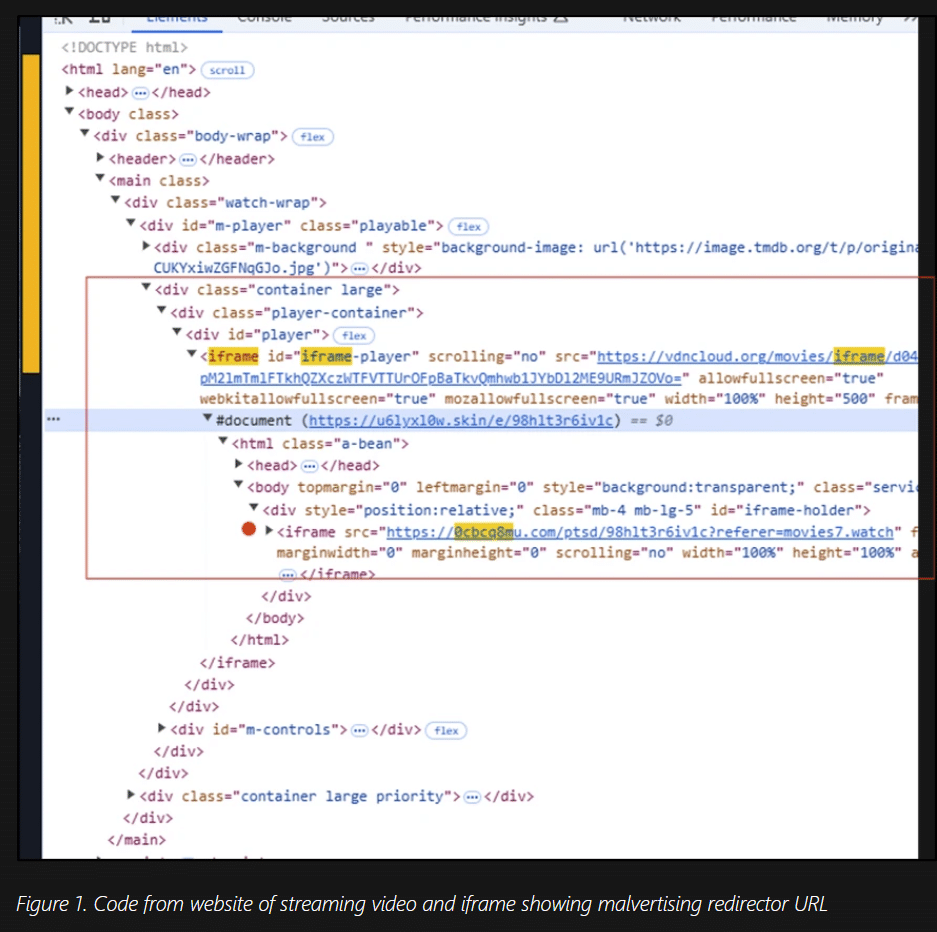
Microsoft says that the attack stemmed from illegal streaming sites where embedded redirectors generated pay-per-view/pay-per-click revenue from malvertising platforms.
“These redirectors subsequently routed traffic through one or two additional malicious redirectors, ultimately leading to another website, such as a malware or tech support scam website,” Microsoft explains.
That was only the beginning.
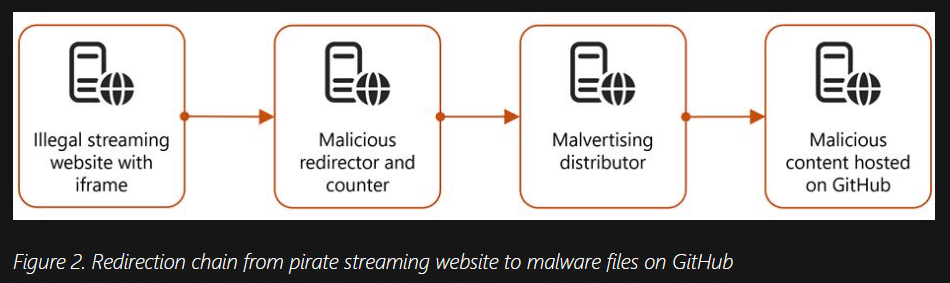
First-Stage Payload
Those scam websites typically redirected users to GitHub where the attackers hosted the first-stage malware payloads. Often digitally signed with newly created certificates, Microsoft says this infection allowed the attackers to establish a dropper for additional payloads hosted elsewhere.
The GitHub repos have since been taken down. Microsoft says it also observed similar activity where Discord and Dropbox delivered the payload.
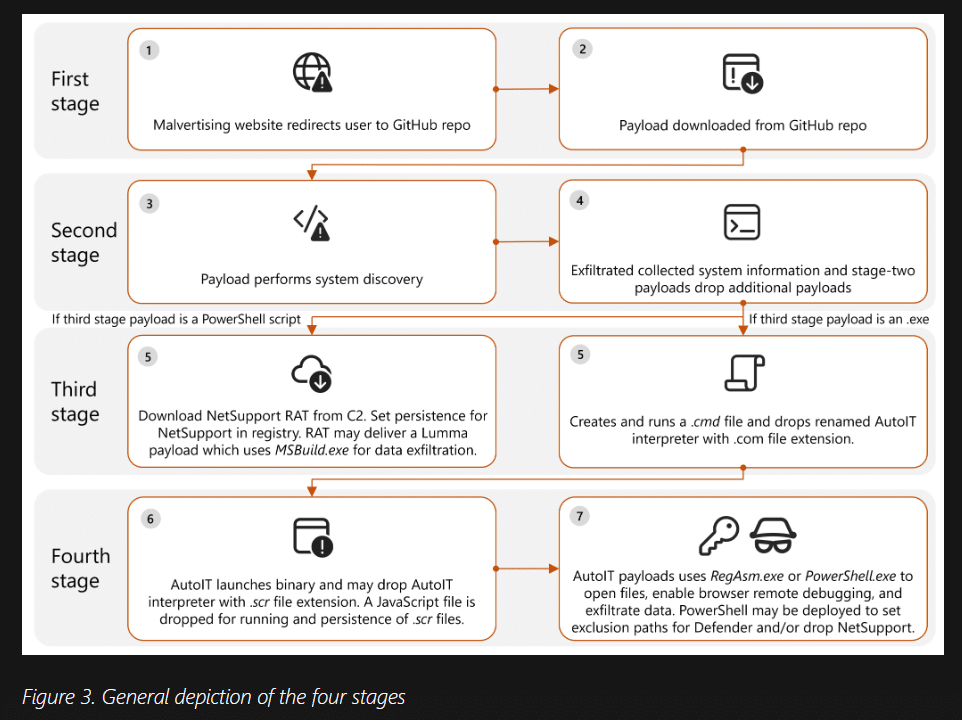
Second, Third, and Fourth-Stage Payloads
During the second stage the attackers engaged in system discovery, obtaining information about the host; memory size, GPU specs, screen resolution, operating system, and user paths, for example. The information was Base64-encoded before being exfiltrated to a remote IP address.
Microsoft says that activity in the Third Stage depended on the payload in the second-stage payload. “Executables and PowerShell scripts were dropped, initiating a chain of command execution, payload delivery, defense evasion, persistence, C2 communication, and data exfiltration,” the company writes.
The fourth-stage, documented in excruciating detail by Microsoft, saw multiple files dropped from various executables, carry out tasks including process injection, remote debugging, data exfiltration through various mechanisms. One file ensured persistence on the host by first dropping an AutoIT .scr file and a .js (JavaScript) with the same name.
“The purpose of the JavaScript file is to ensure persistence by creating a .url internet shortcut that points to the JavaScript file and is placed in the Startup folder, ensuring that the .scr file executes when the .js file executes (through Wscript.exe) upon user sign-in,” Microsoft reports.
Additional mechanisms were also available, including those that established network connections to Telegram and Let’s Encrypt, among others.
“The .scr file can initiate C2 connections, enable remote debugging on Chrome or Edge within a hidden desktop session, or create TCP listening sockets on ports 9220-9229.
“This functionality allows threat actors to monitor browsing activity and interact with an active browser instance. These files can also open sensitive data files, indicating their role in facilitating post-exploitation activities.”
Stealing Information
The multi-stage approach saw the attackers use various files and scripts to collect system and browser information. Information stealers including Lumma Stealer, which is known for targeting gamers with a penchant for mods, and the trojan Doenerium were “commonly deployed” according to Microsoft, alongside use of software already installed on victims’ machines.
“The threat actors incorporated use of living-off-the-land binaries and scripts (LOLBAS) like PowerShell.exe, MSBuild.exe, and RegAsm.exe for C2 and data exfiltration of user data and browser credentials,” the company adds.
Mitigation
Microsoft Defender Antivirus detects these attacks, but Microsoft recommends additional actions to more fully mitigate this type of threat. Windows users should enable tamper protection and network protection, use web browsers with Microsoft Defender SmartScreen, and use AppLocker to restrict prohibited software.
Many rightsholders would advise never visiting pirate sites as the best option for avoiding this type of attack. That would’ve worked here, but the same attack could’ve taken place elsewhere too, so a more proactive approach should also be considered as one of the options available.
Basics include keeping software updated, operating systems and browsers in particular, a good ad blocker turned up to 11, and use of an encrypted password manager in preference to a browser full of plain text credentials.
Backups need no explanation and if possible, a virtual machine should be used for browsing. This reduces the chances of an infection causing havoc on a main system, which should be using an OS downloaded from the official source, not some random pirate site.
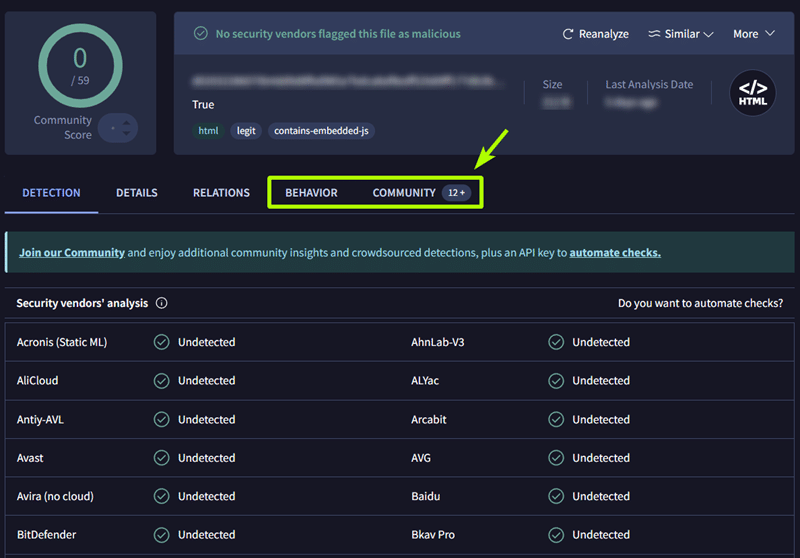
Finally, clean bills of health for sites and apps reported on sites like VirusTotal can be misleading. That’s not because these services are useless, far from it. In many cases the upfront scores/detections just aren’t the right tool for the job.
Advice to look at detection scores for assurances that a site or a piece of software is guaranteed safe, should be given no weight, especially when more useful information is just a click away.
To fully appreciate the scale and scope of the scheme and the commitment of those behind it, it’s worth reading the full report.
Hope you enjoyed this news post.
Thank you for appreciating my time and effort posting news every day for many years.
News posts... 2023: 5,800+ | 2024: 5,700+ | 2025 (till end of February): 874
RIP Matrix | Farewell my friend ![]()



3175x175(CURRENT).thumb.jpg.b05acc060982b36f5891ba728e6d953c.jpg)
Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.